🔐 Crack the Code
Share this article on
Cybersecurity Acronyms Every South African SME Needs to Know
📚 Tools to protect your business from real threats.
In South Africa, cybercrime is no longer just a big-business problem. It’s everyone’s problem. SMEs are especially attractive to attackers because they often lack the right tools or resources.
To stay protected, you don’t need to become a cybersecurity expert. You just need to know which tools to use. That’s why we created this quick acronym guide, packed with real-world examples and local context.
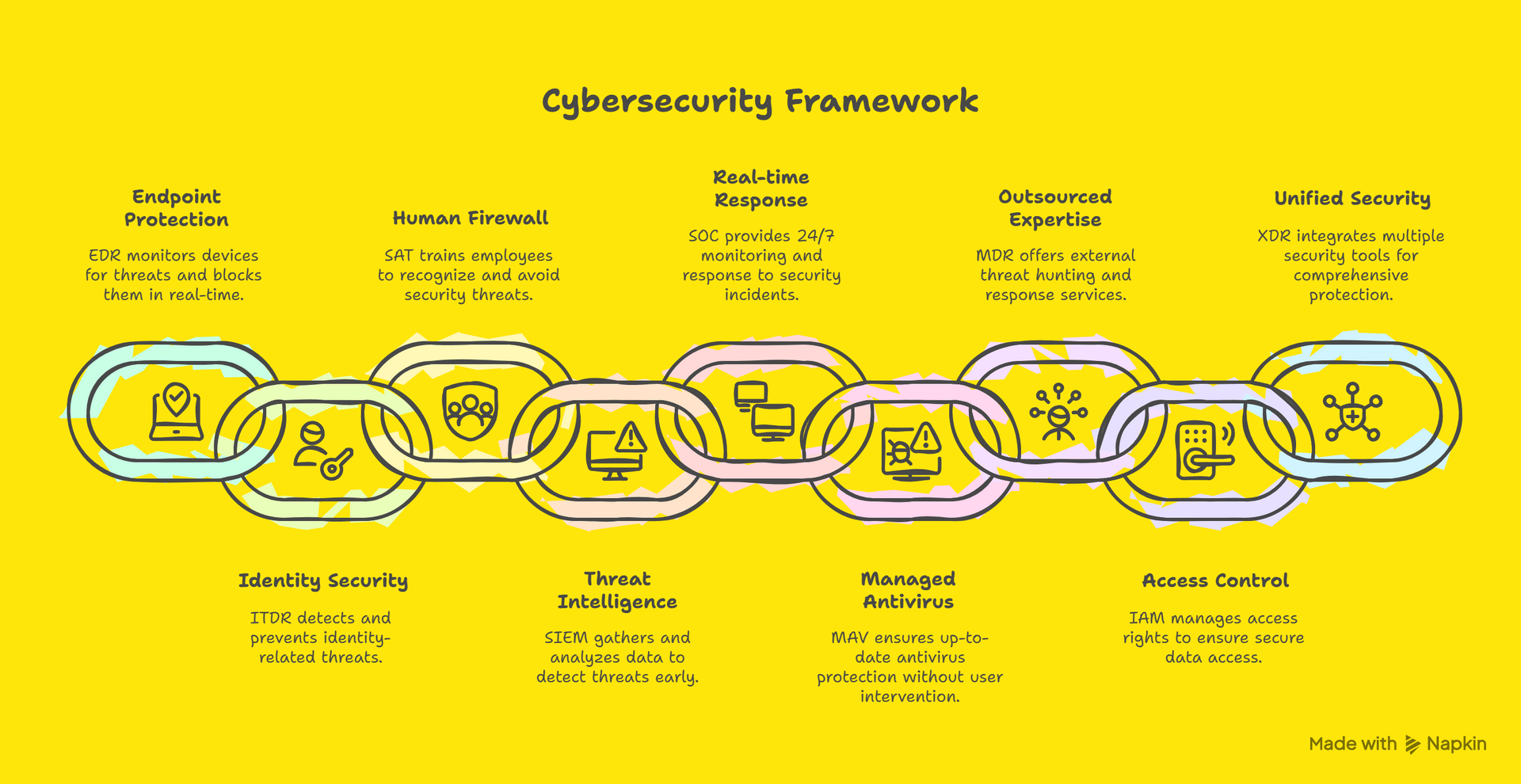
🛡️ EDR – Endpoint Detection & Response
Watches your devices closely and blocks threats in real time.
📍 Example: Your intern opens a sketchy PDF invoice. EDR steps in before ransomware can launch.
🧠 SAT – Security Awareness Training
Your team is your first line of defence. Teach them how to spot threats.
📍 Example: Your receptionist gets a fake billing email from "Vodacom." Because of SAT, she spots the scam and deletes it.
🕵️ ITDR – Identity Threat Detection & Response
Monitors login behaviour and catches identity abuse early.
📍 Example: Someone tries to log into your account from Ukraine at 3 a.m. ITDR locks it before they get in.
📊 SIEM – Security Info & Event Management
Analyzes your system logs and alerts you when things look suspicious.
📍 Example: Your CRM server gets hit with 97 failed login attempts in minutes. SIEM raises the flag before they succeed.
🏢 SOC – Security Operations Centre
A team that monitors your systems around the clock and responds to incidents.
📍 Example: While you're asleep, the SOC stops a brute-force attack and emails you the details with a response summary.
🦠 MAV – Managed Antivirus
Antivirus protection that stays updated and active without you having to think about it.
📍 Example: You insert an old USB drive from a supplier. MAV blocks a virus before it infects your entire system.
🛡️ MDR – Managed Detection & Response
A team of experts keeping an eye on your environment and responding fast when threats appear.
📍 Example: Unusual files are being uploaded to Dropbox. MDR sees it, investigates, and blocks the activity within minutes.
🔑 IAM – Identity & Access Management
Controls who can access specific data or systems at any time.
📍 Example: A junior employee shouldn't have access to payroll data. IAM ensures they never get that far.
🧰 XDR – Extended Detection & Response
Brings together all your security tools into one powerful system.
📍 Example: A phishing email gets through. XDR pulls alerts from email, identity, and device layers to shut it down fast.
🎯 Final Word
Even if your company has just five laptops and a shared WiFi password, these cybersecurity tools matter.
Every acronym in this guide represents a layer of defence that could save your business from financial loss, reputational damage, or both.
Start with what you have, fill in the gaps, and grow your protection as your business grows.
💬 Ready to tighten up your cybersecurity stack?
At Hackerstopped, we help South African SMEs stay protected without breaking the bank.
We provide practical, jargon-free support tailored to your needs.
Cybersecurity for humans.
Simple. Smart. Local.
Make Contact today!



