When Do Hackers Hack?
Share this article on
A Thief in the Night 🕵️♂️🌙

Picture this. You’re fast asleep, curled up under a warm blanket. The only sound is the faint hum of your fridge and maybe a neighbour’s dog giving the occasional half-hearted bark. You’re dreaming about beach holidays, winning the Lotto, or finally telling your boss where to stick that “urgent” Friday afternoon email.
Meanwhile… in a darkened room somewhere across the globe, someone is wide awake. Their “office” is a laptop, a hoodie, and a questionable mug of instant coffee. And you? You’re their project of the night.
Welcome to the reality of modern cybercrime.
🌙 Why Hackers Love the Night Shift
Hackers operate on one simple principle: strike when you’re not looking. The dead of night is perfect for that. While you’re binge-watching your favourite series, out with friends, or sound asleep, they are probing, scanning, and testing your digital defences.
Why at night?
- You’re not paying attention. Obvious, but effective. No one’s logging into their bank app at 3 AM to double-check transactions.
- Response times drop. Your IT team is off-duty, your inbox is closed, and your phone is on silent.
- Global time zones work in their favour. Night for you is prime time for them.
And just like that, your quiet night can become a hacker’s busy shift.
🖥️ While You Sleep…
Here’s a little mental picture.
- At 02:13 AM, your email account gets a login attempt from a location you’ve never even Googled.
- At 02:16 AM, a fake invoice is sent from your account to your clients.
- By 02:23 AM, those clients have opened the email because, surprise, it looks exactly like your real invoices.
You wake up at 07:00, make coffee, and blissfully check your phone… not knowing your reputation has taken a knock while you were still in dreamland.
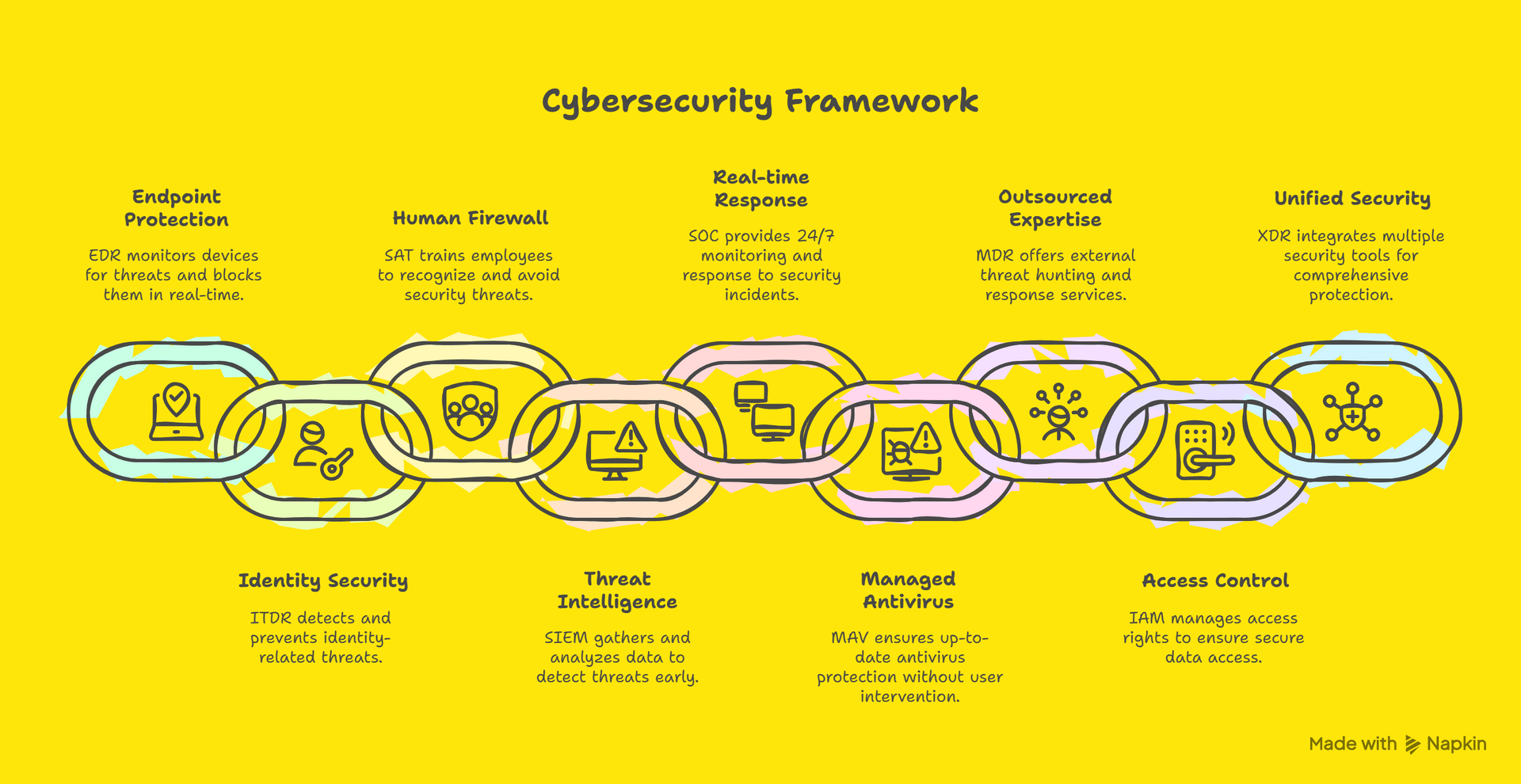
💡 But I Have Antivirus, So I’m Fine… Right?
Antivirus is like locking your front door. Useful? Absolutely. Foolproof? Not even close. A determined intruder will try the windows, pick the lock, or wait until you leave the key under the mat.
The modern hacker toolkit goes far beyond viruses. They use:
- Phishing emails that look frighteningly real.
- Keyloggers that record every tap you make.
- Credential stuffing that uses stolen passwords from other breaches to unlock your accounts.
- Ransomware that locks you out of your own files until you pay up.
The truth? Automated tools will miss things. A human threat analyst won’t.
🛡️ Why Humans Are Still the Best Defence
Let’s be honest. Machines are brilliant, but they’re also literal. They follow rules and scripts. Hackers? They don’t play by the rules.
That’s why human monitoring matters:
- Pattern recognition. A trained analyst spots subtle behaviour changes that software ignores.
- Context awareness. Humans know that “login from Cape Town” at 3 AM is fine if you’re on holiday there… but suspicious if your phone location says you’re still at home in Joburg.
- Creative response. When a threat changes direction, a human pivots instantly.
In short, technology works best with people steering it. That’s why at Hackerstopped, our team watches over your endpoints and your identity 24/7, powered by industry-leading tools like Huntress — but always with human insight in the driver’s seat.
💤 Hackers Count on Your Sleep Schedule
Cybercriminals think of your bedtime as an opportunity window. They know:
- Between 10 PM and 6 AM, fewer people are online.
- Security alerts might go unnoticed for hours.
- Small businesses rarely have round-the-clock IT coverage.
This isn’t paranoia. It’s just smart strategy on their part. If you were planning a break-in, would you choose 2 PM on a busy street or 2 AM when no one’s looking?
📱 The Endpoint Problem
An endpoint is any device that connects to your network. Your laptop, phone, tablet — even that smart coffee machine you bragged about on Instagram. Hackers love endpoints because they’re often the weakest link.
Why?
- People delay updates (because who wants to restart mid-Netflix episode?).
- Devices are used on public Wi-Fi without protection.
- Personal and work accounts get mixed on the same device.
Once a hacker gets in through one endpoint, they can move deeper into your systems. And that’s where the real damage begins.
🔐 Identity Theft: The Long Game
While ransomware grabs headlines, identity theft is the slow burn of cybercrime. Hackers steal personal details, then sit on them. They might:
- Open bank accounts in your name.
- Apply for loans you’ll never see.
- Sell your details on the dark web for someone else to exploit.
And because you’re not constantly checking, the damage can go unnoticed for months.
📊 A Night in the Life of a Hacker
Let’s break down a typical “night shift” from a hacker’s point of view:
20:00 – Log in to a network of compromised machines (botnet).
20:15 – Launch a scan for vulnerable devices in targeted regions.
21:00 – Send a phishing email batch to 2,000 addresses harvested from a recent data leak.
23:00 – Exploit any weak endpoints detected. Install a backdoor.
01:00 – List stolen data on a dark web forum.
03:00 – Deploy ransomware to compromised networks.
04:30 – Disappear, leaving chaos for the morning shift to discover.
And that’s just a Tuesday.
🤝 The 24/7 Protection Mindset
Protection is not just about having the right software. It’s about mindset. A good security posture means:
- Expecting attacks, not being surprised by them.
- Having constant monitoring so you can respond before damage spreads.
- Understanding that security is as much about people as it is about technology.
📣 Hackerstopped: Watching While You Sleep
We believe in keeping things simple. You focus on living your life. We focus on watching your back.
With 24/7 human monitoring, we:
- Track suspicious activity in real time.
- Respond instantly to threats.
- Protect your identity and endpoints from becoming an easy target.
And yes, we’re awake at 3 AM.
🧠 Pro Tips to Make Yourself a Harder Target
Even with professional monitoring, there are habits that make a difference:
- Use strong, unique passwords for every account.
- Enable multi-factor authentication everywhere possible.
- Update your devices without delay.
- Think twice before clicking any link you didn’t expect.
- Back up your data to secure locations regularly.
These may sound basic, but combined with professional oversight, they make a hacker’s job much harder.
🎯 The Takeaway
Hackers are patient, opportunistic, and most active when you’re least alert. They are not movie villains hammering keyboards in neon-lit rooms (although sometimes they are). They are everyday people with extraordinary persistence, armed with the knowledge of how to exploit small mistakes.
You can’t out-stay awake a hacker. You can out-smart them. The key is having skilled humans watching your digital world while you live in the real one.
So next time your head hits the pillow, ask yourself: Who’s watching your back tonight?